Chatbots in Facebook Messenger
The attackers send an email warning to the recipient that their Facebook page has broken community standards giving them 48 hours to appeal the judgement before their page is destroyed. This is the first step in a phishing attempt.
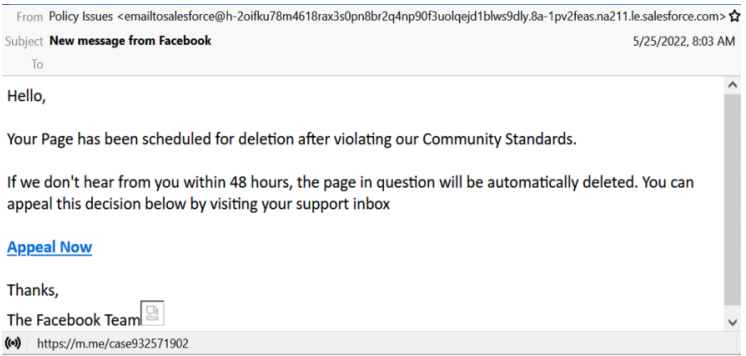
Phishing email sent to random targets (TrustWave)
The user is offered a chance to resolve the problem in Facebook’s Support center, and to access it, they’re urged to click on an “Appeal Now” button.
If the user clicks that button they are directed to a Messenger conversation where a chatbot impersonates a Facebook customer support agent.
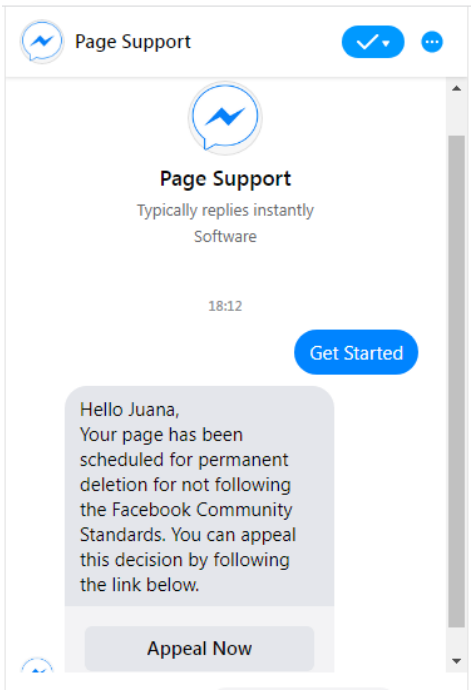
The phishing chatbot on Messenger (TrustWave)
The Facebook page associated with the chatbot is a standard business page with no followers and zero posts. However, if you check the profile you would see a message stating that the profile is “Very responsive to messages,” indicating that it is actively used. Sounding “phishy” yet?
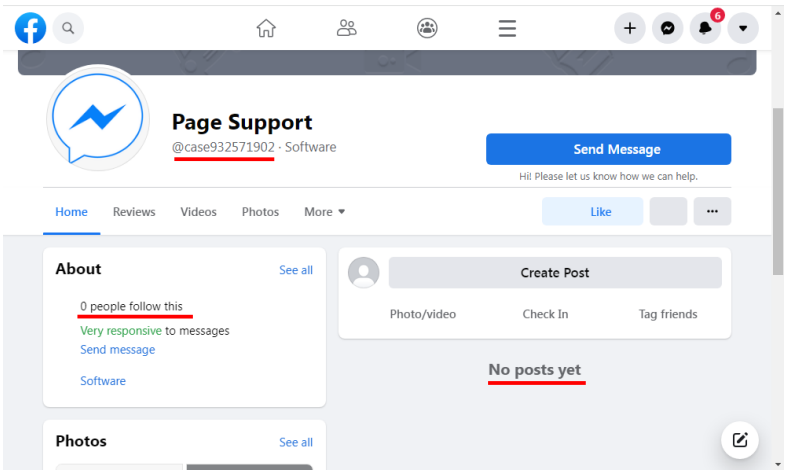
Chatbot’s Facebook account page (TrustWave)
The chatbot will send the user an “Appeal Now” button on Messenger. This will take the victim to a website disguised as a “Facebook Support Inbox,” but the URL is not part of Facebook’s domain.
Additionally, as TrustWave points out, the case number on that website does not correspond to the one given by the chatbot earlier. Despite these facts, consumers in a state of panic are unlikely to discover the fraud due to being in panic mode.
The primary phishing page, which is displayed below, asks users to submit their email address, complete name, page name, and phone number in order to appeal the decision to delete their page.
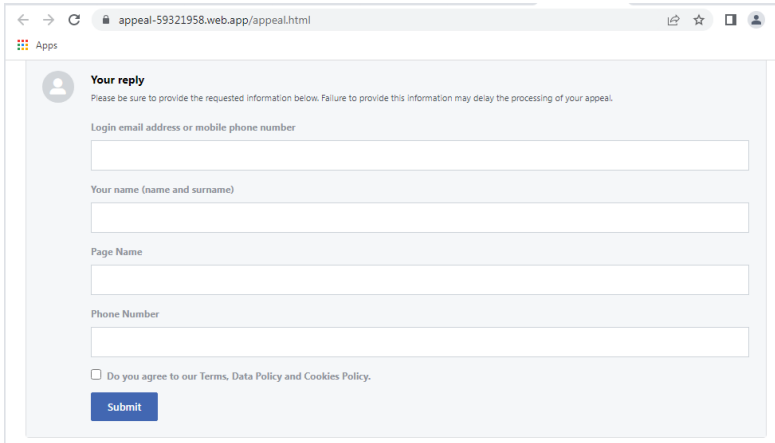
Form requesting user data (TrustWave)
After this data is entered in the fields and the “Submit” button is pressed, a pop-up appears requesting the account password. After that, all information is sent to the threat actor’s database via a POST request.
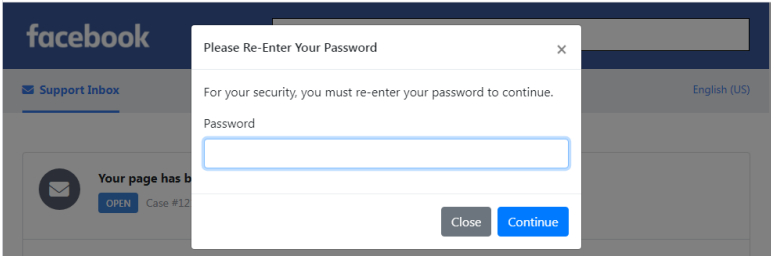
Pop-up window requesting account password (TrustWave)
Finally, a fake 2FA website is accessed and the victim is instructed to enter the OTP they received through SMS on the supplied phone number. That page will accept anything, thus its sole purpose is to give the entire procedure a false air of validity.
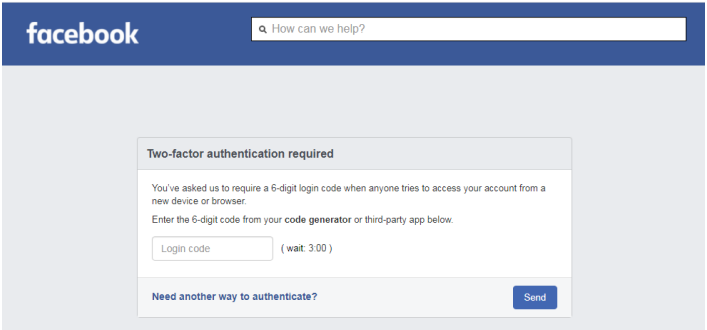
Fake OTP step page (TrustWave)
Following the verification, the victims arrive on a genuine Facebook page with copyright and intellectual property policies that are purportedly pertinent to the user’s breach.
The threat actors must cultivate this erroneous perception of validity in the victims’ thoughts in order to postpone any breach repair steps because the phishing attack is automated and the actual exploitation of the stolen credentials may occur at a later stage.
In phishing attempts, threat actors are increasingly using chatbots to automate the theft of passwords and scale up their operations without expending a lot of time or money.
These scams are more difficult to spot because many websites include AI and chatbots on their support pages, which makes them appear legitimate when users encounter them when opening support cases.
The best line of defence against phishing attacks is to analyze any URLs for pages requesting login credentials, and if the domains do not match the legitimate site’s regular URL, then do not enter any credentials on that site.
If you would like to see how Reis Informatica can help you identify and prevent data breaches from phishing attacks, schedule your complimentary summer business systems assessment with one of our experienced technicians today!
https://www.bleepingcomputer.com/news/security/messenger-chatbots-now-used-to-steal-facebook-accounts/

