Does this sound like a new concept/you haven’t heard of this? Keep reading about this type of attack and how you can stay safe and prevent them.
What is an evil twin attack?
An evil twin attack is a fraudulent Wi-Fi access point that appears to be legitimate, but is set up to eavesdrop on wireless connections. This type of attack is the wireless LAN equivalent of the phishing scam.
Wondering how to make sure you stay cyber safe all throughout the year? Read more here.
The surface for attacks remains largely unprotected from Wi-Fi threats that can result in stolen credentials and sensitive information, as well as backdoor access/malware.
It’s been close to 20 years since IEEE 802.11b was released and the world got the start of Wi-Fi-branded products. However, the Layer 2 attack surface remains highly unprotected from Wi-Fi threats that are dangerous. These threats could result in stolen credentials and sensitive information.
Cyber attackers have been making use of the issue with Wi-Fi. Laptops, phones, and other connected devices aren’t able to differentiate between multiple radios broadcasting the same SSID name. Due to this, hackers are able to use malicious access points (APs) that can listen in on traffic, establish “man-in-the-middle” (MitM) positions, and steal sensitive information – all without leaving any traces.
Evil Twin Attacks
One of the most dangerous Wi-Fi threat categories is Evil Twin attacks. Surprisingly, this attack has been around for almost 2 decades. Recently, the US Department of Justice charged hackers within the Russian military agency with implementing Evil Twin attacks to steal credentials and planted “espionage-oriented malware.” This targeted organizations such as anti-doping agencies, nuclear power operations, and chemical testing labs.
How did these attacks work? The hacked used 802.11 radios that would broadcast the same SSIDs as offices and hotels to trick a victim’s device into associating. This means that their MitM position would be established and would be supplying Internet services through 4G LTE connections to avoid network security.
Below is a closer look at Evil Twin attacks. This way we can better understand visually and the best practices and techniques to use.
Analyzing Evil Twin AP Attacks
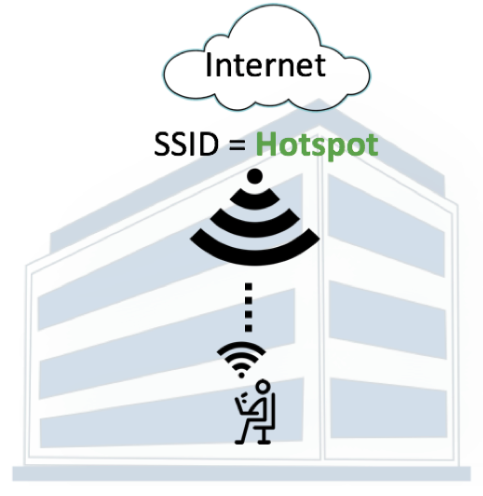
During a normal Wi-Fi connection, an individual’s device (see image below) associates with a legitimate AP.
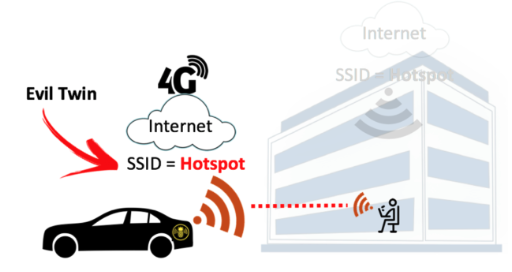
When an Evil Twin AP is present, a hacker broadcasts the same SSID as the legitimate AP (and often the same BSSID or MAC address of the SSID) to fool the device into connecting to the malicious AP (see image below).
In the case of the Evil Twin example we gave earlier, the hackers reportedly used a popular pen-testing tool – Wi-Fi Pineapple from Hak5; which automates a lot of the labour needed to set up this type of attack. This was then connected to gain antennas, battery packs, and a mobile 4G LTE WAN connection that was located in car trunks or carried in backpacks into buildings.
When the attackers were in the range of the SSID that was targeted, they began broadcasting the same SSID. This is pretty straightforward and could be done on smartphones with data that will allow Wi-Fi hotspotting. The hackers would be looking to avoid suspicion to antennas and battery packs. So, they typically choose a popular tool called “bettercap” – can run on Linux, Mac, Windows, Android; configures a fake SSID to be broadcasted.
Also, it’s important to keep in mind that Evil Twin attackers need to use individuals with a radio capable of being in monitoring mode.
If the SSID that is targeted is a busy open hotspot, victims will connect to the Evil Twin AP within seconds. If the target is a private PSK-encrypted SSID, the hacker would need to have the knowledge of the PSK.
Most people choose to auto join to saved Wi-Fi networks. If the hacker can’t trick the victim into connecting the malicious AP, they can break the connection by flooding the legitimate AP with spoofed deauthentication frames – also known as a deauthentication attack. This attack tells the victim that their connection has dropped.
Once the victim has connected to the malicious AP, the attack is complete. The whole process is used to allow the attackers to have MitM positions from where they can drain packets, inject malware, or install backdoors onto the device for remote access.
From here, the hacker has control over the Wi-Fi session. These cyber criminals can leverage tools to duplicate popular login forms for social media sites and email hosting platforms. Then they would intercept the credentials in plain text, forward them to the legitimate website, and log in as the user. What’s scary is that as the user, you might think that you logged into email as usual, but you have actually given the attacker your credentials.
Preventing Evil Twin AP Attacks
Businesses that offer Wi-Fi access to employees and/or customers can use a wireless intrusion prevention systems (WIPS) that will detect the presence of an Evil Twin AP and prevent any managed corporate clients from connecting to them.
For Wi-Fi users, this type of attack is nearly impossible to detect due to the SSID appearing to be legitimate and the attackers usually provide internet service. In most situations, the best way to keep safe is to stay off of Wi-Fi networks that are unfamiliar or to use a VPN to surround the session with another level of security.
Sadly, most of the innovation for Wi-Fi has been limited to elements such as radio range and connectivity instead of security. Without better industry wide emphasis on security for Wi-Fi or criteria for evaluating Wi-Fi security, many networking and security professionals don’t have the clarity they need to prevent threats via Wi-Fi. Education is important, as well as having conversations about level of security and protect we expect and need from Wi-Fi solutions.
We have reached the end of this post.
Hopefully you are able to take away some new learning and apply it in your life. If you have any questions or comments, use the below section.
Looking to keep improving your security? Take a look at our security awareness kit below.
Request Your Complimentary Consultation!
Sources:
Orsi, R. (Author). (2018). Understanding Evil Twin AP Attacks and How to Prevent Them. [Images]. Retrieved January 21, 2020 from https://www.darkreading.com/attacks-breaches/understanding-evil-twin-ap-attacks-and-how-to-prevent-them-/a/d-id/1333240?image_number=3
Orsi, Ryan. (2018). Understanding Evil Twin AP Attacks and How to Prevent Them. Retrieved January 21, 2020 from https://www.darkreading.com/attacks-breaches/understanding-evil-twin-ap-attacks-and-how-to-prevent-them-/a/d-id/1333240