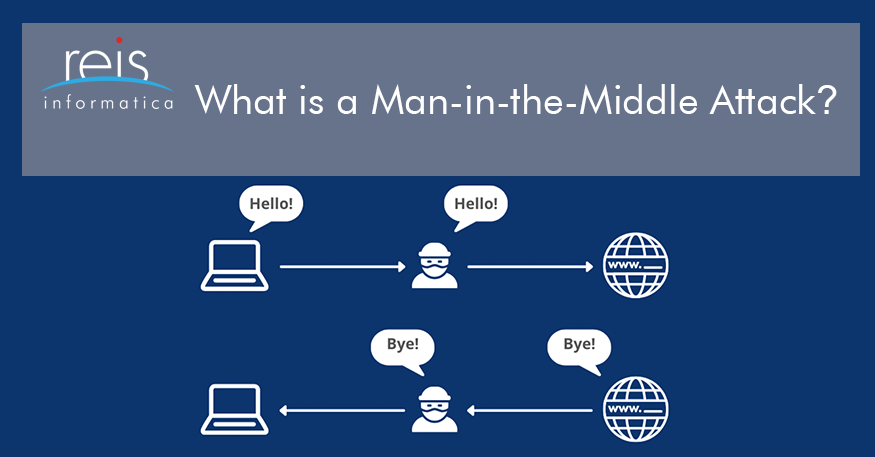
We’re not going to pretend you need a detailed explanation of what a man-in-the-middle (MITM) attack is. It’s as literal as it gets: a targeted attack where a person puts themselves in the middle between you and whatever it is you are trying to communicate with, which is usually a website.
By doing so, they can see and store everything you and your other party are sharing with each other.
The purpose of this post is not to define MITM attacks. But to show you just how easy to set up they are, their devastating consequences, and why you might be closer than you think to be the victim of one.
Let’s take a quick look at the most common MITM attack scenarios. This way, we will be much more effective at trying to prevent them.
Scenario #1 – All Ears:
In the most common type of MITM attack, the attacker will fake the name of a trusted network so you will connect to it without any suspicion.
For example, they can create a fake Wi-Fi network inside a busy coffee shop or office. By using the exact same name, and since public networks are usually open, there would be no reason for you to think it’s fake.
Once you are connected, the attacker will relay all communication between you and the destination. Not without stealing it first, of course.
Now, you might be thinking, that’s not so bad, right? Who cares if someone knows I’m browsing Facebook or checking my email.
Wrong.
Attackers are able to watch, capture, and store any images you see, text you type, or audio you hear, without anything looking suspicious on your end. Talk about scary.
Scenario #2 – I Promise It’s Me:
Unfortunately, more advanced attackers are not satisfied with just capturing the information you are already exchanging, and go one step further.
Since they are in the middle of our communication, hackers can choose to never deliver our message at all, and simply fake the response.
Meaning you might see your bank’s login screen, but in reality, your request never made it there. The attacker shows you a website that looks just like it, and now can ask for any information they want.
After all, it’s not uncommon for your bank to ask for your password, or for government websites to ask for your social insurance number.
The question is, is it really your bank asking?
Why Should I Care?
It’s important to understand that, while sometimes used interchangeably, privacy and security are not the same things. It seems almost futile to try and hide public information from the internet nowadays, so you could understandably not care too much.
Man-in-the-middle attacks, however, compromise your security. They put at risk much more than your browser history.
Your bank accounts, government ID’s, credit card numbers, cryptocurrency wallets, secure documents, and really anything you can store in your computer is up for grabs.
Oh, I almost forgot.
Remember we told you they’re easy to set up?
Well, we meant it. Don’t take my word for it. Take a look at this amazing video from Keatron Evans, where he sets up a MITM attack from scratch and teaches you how to do one, in just 10 minutes!
Safety First, Always
At this point you might be ready to throw away your computer and live off the grid.
No need for extremes.
There are a few easy things you can do to prevent MITM attacks:
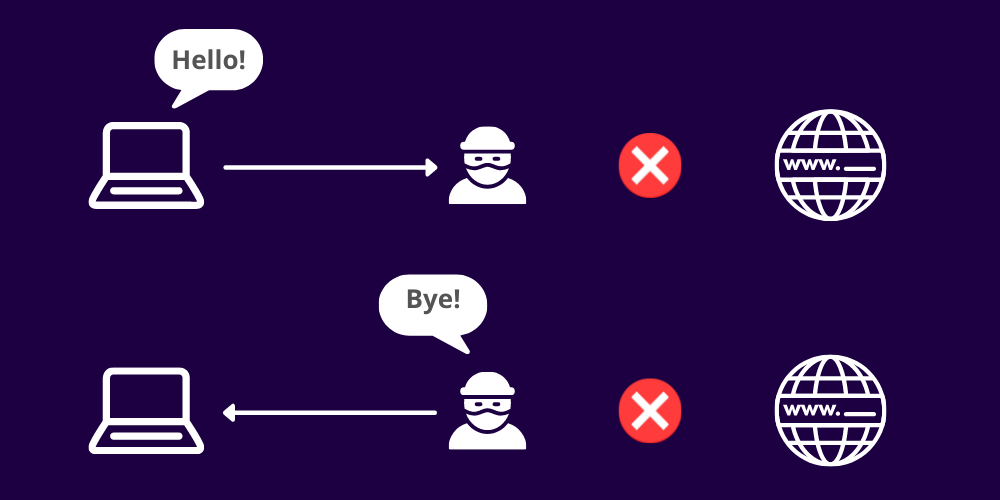
- Don’t connect to public networks: They are as easy to fake as the attacks on them are hard to prevent. There is not much to do besides avoiding them altogether.
We understand that is sometimes easier said than done, what if a public network is your only option? We got you covered.
- Multi-Factor Authentication (MFA): Having an additional method of authentication besides your password, like an SMS text code, is an incredibly effective way of protecting your accounts. More and more websites are making MFA mandatory because of its effectiveness.
Two issues here: First, not all websites or applications offer MFA. On top of that, MITM attackers could also fake an MFA screen and accept any code you input, defeating its purpose.
- VPN Software: Cost-effective, reliable, and easily accessible. It will encrypt your data so no one can read it, even if intercepted on the way. Since connecting to public networks might be unavoidable, and not all websites offer MFA, this is usually your safest bet for maximum peace of mind.
MITM attacks might be easy to create and easier to fall for, but now that you are an expert, there is no excuse for you or your company to be a victim of one.
In the words of Johnny Cash, remember to keep your eyes open all the time.